admin(DCTF)
题目链接:http://web.jarvisoj.com:32792/
打开这道题目只看到了Hello World,查看源码也没有发现有用的东西,但是在这里我们找到robots.txt,根据内容我们构造payload。
http://web.jarvisoj.com:32792/admin_s3cr3t.php
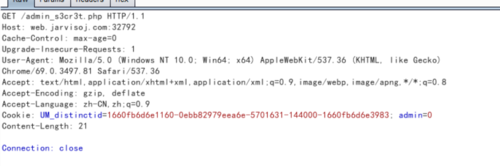
在这里我们看到了一个好像是flag的内容,但是想到题目名称为admin就想到这可能是个伪flag,不过还是要试一下的,因为有时候结果让人意想不到。尝试过后发现果然是伪flag,我们对其进行抓包,
我们修改admin的值为1go一下,得到了flag,这道题目是一道非常简单的web题目,再掌握robots.txt的知识以及抓包改包以后便可以轻松拿下。
WEB?(强网杯)
题目链接:http://web.jarvisoj.com:9891/#/ 题目描述:这么简单的题,是WEB吗?
打开题目第一反应注入题目,然而怎么尝试都不对,于是查看了一下源码发现了突破口(这里说明做题一定不要有惯性思维)我们在源码中看到了app.js不妨进去看一看,搜索password,我们看到了这样一段代码
(self.setState({errmsg:"Wrong Password!!",errcolor:b.red400}),setTimeout(function(){self.setState({errmsg:""})},3e3))})}},{key:"__handleFormChange__REACT_HOT_LOADER__",value:function(e)阅读代码我们可以发现在对password进行验证的时候调用了这样一个函数
__handleFormChange__REACT_HOT_LOADER__
搜索一下这个函数我们可以看到这样一个调用
{key:"__checkpass__REACT_HOT_LOADER__",
value:function(e)
{
if(25!==e.length)
return!1;
for(var t=[],n=0;n<25;n++)
t.push(e.charCodeAt(n));
for(var r=[325799,309234,317320,327895,298316,301249,330242,289290,273446,337687,258725,267444,373557,322237,344478,362136,331815,315157,299242,305418,313569,269307,338319,306491,351259],o=[[11,13,32,234,236,3,72,237,122,230,157,53,7,225,193,76,142,166,11,196,194,187,152,132,135],[76,55,38,70,98,244,201,125,182,123,47,86,67,19,145,12,138,149,83,178,255,122,238,187,221],[218,233,17,56,151,28,150,196,79,11,150,128,52,228,189,107,219,87,90,221,45,201,14,106,230],[30,50,76,94,172,61,229,109,216,12,181,231,174,236,159,128,245,52,43,11,207,145,241,196,80],[134,145,36,255,13,239,212,135,85,194,200,50,170,78,51,10,232,132,60,122,117,74,117,250,45],[142,221,121,56,56,120,113,143,77,190,195,133,236,111,144,65,172,74,160,1,143,242,96,70,107],[229,79,167,88,165,38,108,27,75,240,116,178,165,206,156,193,86,57,148,187,161,55,134,24,249],[235,175,235,169,73,125,114,6,142,162,228,157,160,66,28,167,63,41,182,55,189,56,102,31,158],[37,190,169,116,172,66,9,229,188,63,138,111,245,133,22,87,25,26,106,82,211,252,57,66,98],[199,48,58,221,162,57,111,70,227,126,43,143,225,85,224,141,232,141,5,233,69,70,204,155,141],[212,83,219,55,132,5,153,11,0,89,134,201,255,101,22,98,215,139,0,78,165,0,126,48,119],[194,156,10,212,237,112,17,158,225,227,152,121,56,10,238,74,76,66,80,31,73,10,180,45,94],[110,231,82,180,109,209,239,163,30,160,60,190,97,256,141,199,3,30,235,73,225,244,141,123,208],[220,248,136,245,123,82,120,65,68,136,151,173,104,107,172,148,54,218,42,233,57,115,5,50,196],[190,34,140,52,160,34,201,48,214,33,219,183,224,237,157,245,1,134,13,99,212,230,243,236,40],[144,246,73,161,134,112,146,212,121,43,41,174,146,78,235,202,200,90,254,216,113,25,114,232,123],[158,85,116,97,145,21,105,2,256,69,21,152,155,88,11,232,146,238,170,123,135,150,161,249,236],[251,96,103,188,188,8,33,39,237,63,230,128,166,130,141,112,254,234,113,250,1,89,0,135,119],[192,206,73,92,174,130,164,95,21,153,82,254,20,133,56,7,163,48,7,206,51,204,136,180,196],[106,63,252,202,153,6,193,146,88,118,78,58,214,168,68,128,68,35,245,144,102,20,194,207,66],[154,98,219,2,13,65,131,185,27,162,214,63,238,248,38,129,170,180,181,96,165,78,121,55,214],[193,94,107,45,83,56,2,41,58,169,120,58,105,178,58,217,18,93,212,74,18,217,219,89,212],[164,228,5,133,175,164,37,176,94,232,82,0,47,212,107,111,97,153,119,85,147,256,130,248,235],[221,178,50,49,39,215,200,188,105,101,172,133,28,88,83,32,45,13,215,204,141,226,118,233,156],[236,142,87,152,97,134,54,239,49,220,233,216,13,143,145,112,217,194,114,221,150,51,136,31,198]],n=0;n<25;n++)
{
for(var i=0,a=0;a<25;a++)
i+=t[a]*o[n][a];
f(i!==r[n])
return!1
}
return!0}
} 可以发现这是一个25元一次方程组,我们可以利用python自带的库写出脚本获得flag也可以通过网页在线解方程组得到flag。
点击查看更多内容
1人点赞
评论
共同学习,写下你的评论
评论加载中...
作者其他优质文章
正在加载中
感谢您的支持,我会继续努力的~
扫码打赏,你说多少就多少
赞赏金额会直接到老师账户
支付方式
打开微信扫一扫,即可进行扫码打赏哦